给个流量包,是个cs流量
按照标准流程分析,提取beacon,用1786.py解密
https://www.freebuf.com/articles/system/327060.html
![图片[1]-西湖论剑2025 cscs write up-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2025/01/image-1024x482.png)
获得公钥,公钥form hex to b64,加个上下框,转成如下内容
-----BEGIN PUBLIC KEY-----
MIGeMA0GCSqGSIb3DQEBAQUAA4GMADCBiAKBgFJeF4Hy8C0TKngYptJput2/OTUsjSApDsIpT75N
d+ZUnvR2bYsOFiAACt+9ev+ZzXLwViPrDe8gImXPYx3YlazV6YHahCTAOilYlcgZSjFkHy7s1ahx
XKic2/lDPF1DdTh2dmbDvbD4YpVVN1tXT+QIqUroL5KWAIXUFjdPFlSzAgMBAAE=
-----END PUBLIC KEY-----用cookie尝试用cs-decrypt-metadata发现解不开。
![图片[2]-西湖论剑2025 cscs write up-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2025/01/image-2-1024x408.png)
想起来网鼎杯出过已知公钥算私钥的题,照流程走一遍
https://1cepeak.cn/posts/wdb2024-turtle-writeup/#misc
算出来私钥
-----BEGIN RSA PRIVATE KEY-----
MIICWgIBAAKBgFJeF4Hy8C0TKngYptJput2/OTUsjSApDsIpT75Nd+ZUnvR2bYsO
FiAACt+9ev+ZzXLwViPrDe8gImXPYx3YlazV6YHahCTAOilYlcgZSjFkHy7s1ahx
XKic2/lDPF1DdTh2dmbDvbD4YpVVN1tXT+QIqUroL5KWAIXUFjdPFlSzAgMBAAEC
gYApWVrrvY2c0zZKu/VjQ/ivQUPy0b63GmVyS1Lg8frzAiAaESnE2Pl6bwsGbxTE
I+3jeYuE1IdWOAeMnKPhY80fOSgws6vSri7CcxnMUEEn3AMw4YSwBIaBGkdLnfxf
pbS/kUUb/z7/A1SRtNq1n4hZYinnG2NpUuiO1WqwHqOGoQJBAJE14+VVt8ONGIZ1
qIf4cqAnAmtonPhyDNdYZQC0IlxNzyixo/lnlTc80b3jYUA4w8GGQQZea70op4RS
fIJV420CQQCRNePlVbfDjRiGdaiH+HKgJwJraJz4cgzXWGUAtCJcTc8osaP5Z5U3
PNG942FAOMPBhkEGXmu9KKeEUnyCVeSfAkB6vJQuKe+zaDVMoXKbyxIH8DEJXFkh
XjUgZ+SnXZqVbmclPFEe48Cp+cxGtkRjJhfAIZwgp/pk3lIJdDctay9ZAkAhlDeu
CcNj6hXYyg592tsO49ZwZhGedik4Bw3cOsuTUr7r5yBHBUgBLQRHh/QuOLIz50rU
ITOC24rZU4XNUfV7AkAipEfvmXf4RaJLlIoWZe/XkNXpGcsYIeaedUv29xqaNAbA
7HhEs3twu6+G0QP1YuAPNp28FNoe52XfJhVWTw1D
-----END RSA PRIVATE KEY-----然后拿去再用Beacon_metadata_RSA_Decrypt.py去解cookie获得
SHARED_KEY = binascii.unhexlify("9fe14473479a283821241e2af78017e8")
HMAC_KEY = binascii.unhexlify("1e3d54f1b9f0e106773a59b7c379a89d")
然后用CS_Task_AES_Decrypt.py提取最大的包,解密出获得流量文件
'''
cobaltstrike任务解密
'''
import hmac
import binascii
import base64
import struct
import hexdump
from Crypto.Cipher import AES
def compare_mac(mac, mac_verif):
if mac == mac_verif:
return True
if len(mac) != len(mac_verif):
print
"invalid MAC size"
return False
result = 0
for x, y in zip(mac, mac_verif):
result |= x ^ y
return result == 0
def decrypt(encrypted_data, iv_bytes, signature, shared_key, hmac_key):
if not compare_mac(hmac.new(hmac_key, encrypted_data, digestmod="sha256").digest()[0:16], signature):
print("message authentication failed")
return
cypher = AES.new(shared_key, AES.MODE_CBC, iv_bytes)
data = cypher.decrypt(encrypted_data)
return data
def readInt(buf):
return struct.unpack('>L', buf[0:4])[0]
# 接收到的任务数据
shell_whoami= ""
if __name__ == "__main__":
# key源自Beacon_metadata_RSA_Decrypt.py
SHARED_KEY = binascii.unhexlify("9fe14473479a283821241e2af78017e8")
HMAC_KEY = binascii.unhexlify("1e3d54f1b9f0e106773a59b7c379a89d")
enc_data = base64.b64decode(shell_whoami)
print("数据总长度:{}".format(len(enc_data)))
signature = enc_data[-16:]
encrypted_data = enc_data[:-16]
iv_bytes = bytes("abcdefghijklmnop",'utf-8')
dec = decrypt(encrypted_data,iv_bytes,signature,SHARED_KEY,HMAC_KEY)
counter = readInt(dec)
print("时间戳:{}".format(counter))
decrypted_length = readInt(dec[4:])
print("任务数据包长度:{}".format(decrypted_length))
data = dec[8:len(dec)]
print("任务Data")
print(hexdump.hexdump(data))
# 任务标志
Task_Sign=data[0:4]
print("Task_Sign:{}".format(Task_Sign))
# 实际的任务数据长度
Task_file_len = int.from_bytes(data[4:8], byteorder='big', signed=False)
print("Task_file:{}".format(Task_file_len))
with open('data.bin', 'wb') as f:
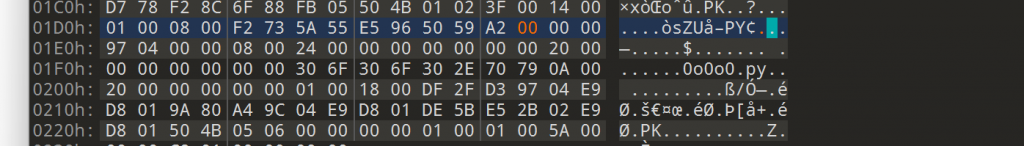
f.write(data[8:Task_file_len])
print(hexdump.hexdump(data[Task_file_len:]))![图片[3]-西湖论剑2025 cscs write up-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2025/01/image-3-828x1024.png)
保存为1.pcap,开始分析
打开发现是cs1.6的流量
![图片[4]-西湖论剑2025 cscs write up-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2025/01/image-4-1024x822.png)
接下来就是抄袭的原题了
https://www.anquanke.com/post/id/261339
直接拉到最下面复制脚本运行即可
![图片[5]-西湖论剑2025 cscs write up-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2025/01/image-5-1024x652.png)
![图片[6]-西湖论剑2025 cscs write up-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2025/01/image-6-1024x131.png)
高手。
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END














暂无评论内容