![图片[1]-CISCN2022初赛个人writeup-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2022/05/image-57-1024x435.png)
又一年ciscn,,,啊,开摆,连续三次都是做到最后一步了,一二三血就都出了,哎呀急死我了呜呜呜,区块链一直没时间看,后续复现一下。该说不说,做题体验还行,跟往届比的话。至少不像去年那种嗯造高考了。
问卷
问卷
ez_usb
流量分析,可以看见是常规usb,直接提取发现rar不太行,然后发现
![图片[2]-CISCN2022初赛个人writeup-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2022/05/image-58-1024x232.png)
存在两种usb的arr,所以猜测是两个键盘,分别提取 usb.addr == "2.10.1" && usbhid.data usb.addr == "2.8.1" && usbhid.data 然后导出csv。然后
cat 111.csv | cut -d "," -f 7 | sed ':a;N;$!ba;s/"//g' > HEXDUMP.txt
cat 222.csv | cut -d "," -f 7 | sed ':a;N;$!ba;s/"//g' > HEXDUMP2.txt
分别导出两个,然后屑exp
str_data = {0x04: "A", 0x05: "B", 0x06: "C", 0x07: "D", 0x08: "E", 0x09: "F", 0x0A: "G", 0x0B: "H", 0x0C: "I",
0x0D: "J", 0x0E: "K", 0x0F: "L", 0x10: "M", 0x11: "N", 0x12: "O", 0x13: "P", 0x14: "Q", 0x15: "R",
0x16: "S", 0x17: "T", 0x18: "U", 0x19: "V", 0x1A: "W", 0x1B: "X", 0x1C: "Y", 0x1D: "Z", 0x1E: "1",
0x1F: "2", 0x20: "3", 0x21: "4", 0x22: "5", 0x23: "6", 0x24: "7", 0x25: "8", 0x26: "9", 0x27: "0",
0x28: "\n", 0x2a: "[DEL]", 0X2B: " ", 0x2C: " ", 0x2D: "-", 0x2E: "=", 0x2F: "[", 0x30: "]", 0x31: "\\",
0x32: "~", 0x33: ";", 0x34: "'", 0x36: ",", 0x37: ".", 0x38: "/", 0x57: "+", 0x5a: "2", 0x5b: "3", 0x5c: "4", 0x5d: "5",
0x5e: "6", 0x5f: "7", 0x60: "8", 0x61: "9"}
nums = []
keys = open('HEXDUMP2.txt')
for line in keys:
if int('0x' + line[4:6], 16) < 0x04 or int('0x' + line[4:6], 16) > 0xa0:
continue
nums.append(int(line[4:6], 16))
keys.close()
print(nums)
output = ""
flag = 0
for n in nums:
if flag == 0:
if n == 0x39:
flag = 1
continue
else:
output += str_data[n].lower()
elif flag == 1:
if n == 0x39:
flag = 0
continue
else:
output += str_data[n].upper()
else:
print('error')
break
print('output:\n' + output)
跑两次就行了。
![图片[3]-CISCN2022初赛个人writeup-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2022/05/image-59-1024x508.png)
上面的复制到010,是rar,下面的是密码,解压后获得flag
![图片[4]-CISCN2022初赛个人writeup-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2022/05/image-60-1024x212.png)
补充:
![图片[5]-CISCN2022初赛个人writeup-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2022/05/image-61-1024x629.png)
wireshark设置方式(
everlasting_night
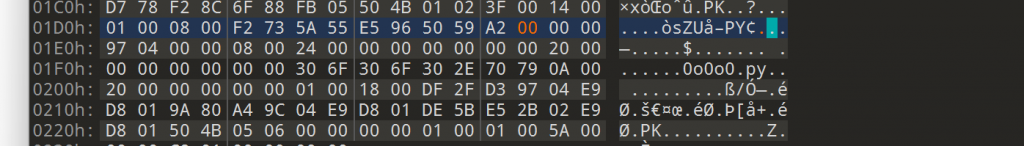
一个图片,010打开发现最后有一串东西,暂时不知道是啥 然后图片a2通道发现一串隐写字符
![图片[6]-CISCN2022初赛个人writeup-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2022/05/image-62.png)
直接用stegsolve发现解不开,手工读一下罢,获得内容 f78dcd383f1b574b
不知道有啥用,fuzz了好久,发现用老python2 的lsb.py可以提取出一个zip。zip有密码。。。好套。 然后fuzz了一波,发现scmd5可以搞出来个密码,尝试解密
![图片[7]-CISCN2022初赛个人writeup-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2022/05/image-63-1024x440.png)
解开了,一个flag文件,010打开内容比较混乱,猜测是需要修复的,改名为flag.data,导入gimp进行修复即可
babydisk
取证大师一把梭,获取wav文件和secret, wav文件常规测试没有发现什么内容,再deepsound发现存在密码,但是没找到相关线索,猜测爆破 deepsound2join.py
#!/usr/bin/env python3
'''
deepsound2john extracts password hashes from audio files containing encrypted
data steganographically embedded by DeepSound (http://jpinsoft.net/deepsound/).
This method is known to work with files created by DeepSound 2.0.
Input files should be in .wav format. Hashes can be recovered from audio files
even after conversion from other formats, e.g.,
ffmpeg -i input output.wav
Usage:
python3 deepsound2john.py carrier.wav > hashes.txt
john hashes.txt
This software is copyright (c) 2018 Ryan Govostes <rgovostes@gmail.com>, and
it is hereby released to the general public under the following terms:
Redistribution and use in source and binary forms, with or without
modification, are permitted.
'''
import logging
import os
import sys
import textwrap
def decode_data_low(buf):
return buf[::2]
def decode_data_normal(buf):
out = bytearray()
for i in range(0, len(buf), 4):
out.append((buf[i] & 15) << 4 | (buf[i + 2] & 15))
return out
def decode_data_high(buf):
out = bytearray()
for i in range(0, len(buf), 8):
out.append((buf[i] & 3) << 6 | (buf[i + 2] & 3) << 4 \
| (buf[i + 4] & 3) << 2 | (buf[i + 6] & 3))
return out
def is_magic(buf):
# This is a more efficient way of testing for the `DSCF` magic header without
# decoding the whole buffer
return (buf[0] & 15) == (68 >> 4) and (buf[2] & 15) == (68 & 15) \
and (buf[4] & 15) == (83 >> 4) and (buf[6] & 15) == (83 & 15) \
and (buf[8] & 15) == (67 >> 4) and (buf[10] & 15) == (67 & 15) \
and (buf[12] & 15) == (70 >> 4) and (buf[14] & 15) == (70 & 15)
def is_wave(buf):
return buf[0:4] == b'RIFF' and buf[8:12] == b'WAVE'
def process_deepsound_file(f):
bname = os.path.basename(f.name)
logger = logging.getLogger(bname)
# Check if it's a .wav file
buf = f.read(12)
if not is_wave(buf):
global convert_warn
logger.error('file not in .wav format')
convert_warn = True
return
f.seek(0, os.SEEK_SET)
# Scan for the marker...
hdrsz = 104
hdr = None
while True:
off = f.tell()
buf = f.read(hdrsz)
if len(buf) < hdrsz: break
if is_magic(buf):
hdr = decode_data_normal(buf)
logger.info('found DeepSound header at offset %i', off)
break
f.seek(-hdrsz + 1, os.SEEK_CUR)
if hdr is None:
logger.warn('does not appear to be a DeepSound file')
return
# Check some header fields
mode = hdr[4]
encrypted = hdr[5]
modes = {2: 'low', 4: 'normal', 8: 'high'}
if mode in modes:
logger.info('data is encoded in %s-quality mode', modes[mode])
else:
logger.error('unexpected data encoding mode %i', modes[mode])
return
if encrypted == 0:
logger.warn('file is not encrypted')
return
elif encrypted != 1:
logger.error('unexpected encryption flag %i', encrypted)
return
sha1 = hdr[6:6+20]
print('%s:$dynamic_1529$%s' % (bname, sha1.hex()))
if __name__ == '__main__':
import argparse
parser = argparse.ArgumentParser()
parser.add_argument('--verbose', '-v', action='store_true')
parser.add_argument('files', nargs='+', metavar='file',
type=argparse.FileType('rb', bufsize=4096))
args = parser.parse_args()
if args.verbose:
logging.basicConfig(level=logging.INFO)
else:
logging.basicConfig(level=logging.WARN)
convert_warn = False
for f in args.files:
process_deepsound_file(f)
if convert_warn:
print(textwrap.dedent('''
---------------------------------------------------------------
Some files were not in .wav format. Try converting them to .wav
and try again. You can use: ffmpeg -i input output.wav
---------------------------------------------------------------
'''.rstrip()), file=sys.stderr)
爆破获得密码 feedback 解密获得key.txt,内容为e575ac894c385a6f,
![图片[9]-CISCN2022初赛个人writeup-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2022/05/image-64-1024x158.png)
取证大师看见文件发现是truecrypt文件,
导出后用刚刚获得的key.txt解密 解密后导入,发现一个zip文件
![图片[10]-CISCN2022初赛个人writeup-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2022/05/image-65-1024x257.png)
导出后无法直接打开,010查看可以发现整体文件时比较混乱的,结合spiral这个文件名,猜测是进行了螺旋加密,写脚本解密即可
from struct import pack
file = open('spiral.zip', 'rb').read()
rotate = 0
match = ((0, 1), (1, 0), (0, -1), (-1, 0))
wall = [0, 86, 86 ,0]
sets = (1, -1, -1, 1)
matrix = []
for i in range(87):
list = []
for o in range(87):
list.append(0)
matrix.append(list)
x = 0
y = 0
for i in file:
matrix[y][x] = i
x += match[rotate][1]
y += match[rotate][0]
if x > wall[1] or x < wall[3] or y > wall[2] or y < wall[0]:
x -= match[rotate][1]
y -= match[rotate][0]
wall[rotate] += sets[rotate]
rotate = (rotate + 1) % 4
x += match[rotate][1]
y += match[rotate][0]
file3 = open('out.zip', 'wb')
for i in matrix:
for o in i:
file3.write(pack('B', o))
file3.close()导出结果后解压获得图片
![图片[11]-CISCN2022初赛个人writeup-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2022/05/image-66.png)
获得内容,当然肯定也要转到低了,由于数量没多少,这里手工转一下就行了,前面的ohhhhhh是给定位的,总共49个字符,开根号得7,7x7,获得最终结果
![图片[12]-CISCN2022初赛个人writeup-魔法少女雪殇](https://cdn.snowywar.top/wp-content/uploads/2022/05/image-67.png)
flag{701fa9fe-63f5-410b-93d4-119f96965be6}














- 最新
- 最热
只看作者