内置了vol3,直接用在线机器做取证就行了
房间链接:TryHackMe | Volatility
一些无关紧要的内容我 就不写了,题目描述也不写了,直接写过程指令就行了,
题目信息:
Case 001 – BOB! THIS ISN’T A HORSE!
Your SOC has informed you that they have gathered a memory dump from a quarantined endpoint thought to have been compromised by a banking trojan masquerading as an Adobe document. Your job is to use your knowledge of threat intelligence and reverse engineering to perform memory forensics on the infected host.
You have been informed of a suspicious IP in connection to the file that could be helpful. 41.168.5.140
The memory file is located in /Scenarios/Investigations/Investigation-1.vmem
Case 002 – That Kind of Hurt my Feelings
You have been informed that your corporation has been hit with a chain of ransomware that has been hitting corporations internationally. Your team has already retrieved the decryption key and recovered from the attack. Still, your job is to perform post-incident analysis and identify what actors were at play and what occurred on your systems. You have been provided with a raw memory dump from your team to begin your analysis.
The memory file is located in /Scenarios/Investigations/Investigation-2.raw
解题与问题:
Answer the questions belowWhat is the build version of the host machine in Case 001?
2600.xpsp.080413-2111
直接python3 vol.py -f /Scenarios/Investigations/Investigation-1.vmem windows.info即可
![图片[1]-Tryhackme Volatility writeup-魔法少女雪殇](https://www.snowywar.top/wp-content/uploads/2023/05/image-1024x462.png)
At what time was the memory file acquired in Case 001?
2012-07-22 02:45:08
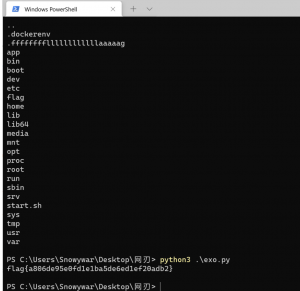
What process can be considered suspicious in Case 001?
reader_sl.exe
python3 vol.py -f /Scenarios/Investigations/Investigation-1.vmem windows.pstree
询问哪个进程可疑
![图片[2]-Tryhackme Volatility writeup-魔法少女雪殇](https://www.snowywar.top/wp-content/uploads/2023/05/image-1-1024x289.png)
What is the parent process of the suspicious process in Case 001?
explorer.exe
问的是父进程,所以还是pstree就行了
What is the PID of the suspicious process in Case 001?
1640
What is the parent process PID in Case 001?
1484
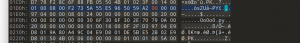
strings大法好
strings /Scenarios/Investigations/Investigation-1.vmem |grep -i “user-agent”
![图片[3]-Tryhackme Volatility writeup-魔法少女雪殇](https://www.snowywar.top/wp-content/uploads/2023/05/image-4-1024x266.png)
What user-agent was employed by the adversary in Case 001?
Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 6.0; en-US)
Was Chase Bank one of the suspicious bank domains found in Case 001? (Y/N)
Y
What suspicious process is running at PID 740 in Case 002?
@WanaDecryptor@
还是pstree,不截图了
What is the full path of the suspicious binary in PID 740 in Case 002?
\Intel\ivecuqmanpnirkt615\@WanaDecryptor@.exe
![图片[4]-Tryhackme Volatility writeup-魔法少女雪殇](https://www.snowywar.top/wp-content/uploads/2023/05/image-5-1024x82.png)
What is the parent process of PID 740 in Case 002?
tasksche.exe
What is the suspicious parent process PID connected to the decryptor in Case 002?
1940
From our current information, what malware is present on the system in Case 002?
wannacry
What DLL is loaded by the decryptor used for socket creation in Case 002?
ws2_32.dll
Threat Spotlight: Inside the WannaCry Attack (blackberry.com)
What mutex can be found that is a known indicator of the malware in question in Case 002?
MsWinZonesCacheCounterMutexA
What plugin could be used to identify all files loaded from the malware working directory in Case 002?
windows.filescan








暂无评论内容